
If your business network is left unprotected, it's a sitting duck. Every day, countless cyber threats are looking for an open door, and without a solid firewall, you're essentially leaving the front door unlocked. A modern firewall isn't just another IT expense; it’s the bedrock of your defense, the one thing standing between your business staying safe and becoming another data breach headline.
Your Digital Fortress Against Modern Cyber Threats
Think of your business network as a medieval fortress. Inside are your treasures: sensitive company data, customer information, and financial records. Every connection—an employee checking email, a customer visiting your site—is someone asking to be let through the main gate. Without a guard, who knows who’s wandering in?
That’s exactly what a firewall does. It’s your elite security detail, posted at every digital entry point. But it’s not just a simple gatekeeper checking a list. It's an intelligent guard that scrutinizes the credentials of every bit of traffic coming in and going out, all based on a strict set of rules you define. It lets the good guys pass and slams the gate on anyone who looks even remotely suspicious.
The Modern Gatekeeper for Your Data
This constant inspection is what keeps your digital environment secure. The firewall looks at "data packets"—the tiny pieces of information zipping across your network—to make sure they meet your security standards. If a packet comes from a shady source or is acting strangely, it’s blocked on the spot. This kind of active filtering is non-negotiable for:
- Preventing Unauthorized Access: It keeps hackers and malicious software from sneaking onto your network and getting their hands on sensitive files.
- Stopping Malware Infections: It acts as a shield, stopping viruses, ransomware, and spyware before they can ever touch your systems.
- Securing Remote Connections: It ensures that when your team works from home or on the road, their connection is secure and doesn't accidentally introduce new threats.
In a bustling economic hub like the UAE, businesses are constantly targeted by cyberattacks. Relying on basic, out-of-the-box protection, like the default firewall on your operating system, is like trying to protect that fortress with a flimsy wooden fence. It might stop a stray animal, but it won’t do much against a determined army.
A properly configured firewall is the foundation of any serious cybersecurity plan. It’s not a passive wall; it’s an active system that monitors, filters, and reports on everything happening on your network, giving you the control to stop threats before they do any real harm.
In the end, recognizing the vital role a firewall plays is the first real step toward building a resilient business. It’s about moving from a reactive "hope for the best" approach to a proactive one where your defenses are truly ready for the threats you will face. Without this critical layer, your data, your reputation, and your entire business are left dangerously exposed.
Navigating the MENA Region's Unique Threat Landscape
Cybersecurity isn't a one-size-fits-all problem. The threats a business faces in one part of the world can look completely different from those somewhere else. For any company with a foothold in the Middle East and North Africa (MENA), understanding the local threat landscape is more than a good idea—it's essential for survival.
This region, especially hubs like the UAE, is a global center for finance, energy, and trade. That distinction also puts a massive target on its back.
A generic security plan simply won't cut it here. Threats in the MENA region are often more targeted, persistent, and driven by motives that go far beyond a simple smash-and-grab for cash. Relying on basic protection is like trying to navigate Dubai with a map of London; you’re completely unprepared for the reality on the ground.
The Rise of Geopolitically Motivated Attacks
The complex geopolitics of the MENA region spill over directly into the digital world, creating a uniquely aggressive cyber threat climate. State-sponsored groups and hacktivists regularly use cyberattacks as a tool to push political agendas, turning corporate networks into digital battlegrounds.
These aren't random acts of vandalism. We're talking about highly coordinated campaigns designed to cripple critical infrastructure or steal sensitive government and commercial secrets. For businesses, this means the risk of becoming collateral damage—or a direct target—is frighteningly high.
One of the most common weapons we see is the Distributed Denial-of-Service (DDoS) attack. Think of it like a mob of thousands of people trying to cram through a single doorway all at once. The entrance gets blocked, and no one with a legitimate reason to enter can get through. A DDoS attack does the same thing to your servers, flooding them with so much junk traffic that your website and online services grind to a halt.
In the first quarter of the year, the MENA region saw a shocking 183% year-on-year increase in DDoS attacks, a surge directly linked to geopolitical tensions and hacktivism. The UAE was hit particularly hard, absorbing 21% of the attacks. You can dig deeper into these numbers in the MENA Cyber Summit 2025 Annual Report.
This isn't just a statistic; it's a warning shot. It shows how regional conflicts are directly translating into digital assaults on businesses. A strong firewall is your first line of defense, designed to spot and filter out this malicious traffic before it can take you offline.
High-Stakes Industries Under Fire
Certain industries in the region are squarely in the crosshairs, targeted for their critical importance and the value of the data they hold. Attackers know that disrupting these sectors can cause massive economic and social chaos, making them prime targets for both extortion and political statements.
Key sectors facing the most heat include:
- Finance and Banking: These institutions are a constant target for sophisticated ransomware gangs demanding huge payouts and cybercriminals looking to steal financial data.
- Energy and Utilities: As the backbone of the region's economy, the energy sector is a magnet for state-sponsored groups focused on espionage or disruption. This industry has seen attacks skyrocket by a staggering 206% year-over-year.
- Government and Public Services: Holding troves of sensitive citizen data, public sector agencies are prime targets for espionage and attacks designed to cause widespread disruption.
If you operate in or do business with any of these industries, the question isn't if you'll be targeted, but when. This is where the role of a firewall becomes crystal clear. An advanced, modern firewall does more than just block traffic; it provides the deep packet inspection and threat intelligence needed to identify and stop attacks specifically tailored to this region. It’s not just a technical box to check—it’s a strategic necessity for staying afloat in one of the world's most challenging cyber environments.
Choosing the Right Type of Firewall for Your Business
Picking the right firewall isn’t a one-size-fits-all kind of deal. The best choice really hinges on your company's size, how complex your network is, and what kind of risks you're up against. It’s crucial to understand that not all firewalls are created equal, and knowing the core differences is the first step to making a smart security investment.
Let’s start with the basics.
From Simple Gatekeepers to Intelligent Guards
Think of the most fundamental option, the Packet-Filtering Firewall, as a simple security guard at the front desk of an office. This guard only glances at the most basic details of each data packet—like where it’s from and where it’s going—and checks it against a list of approved visitors. It's quick and doesn't slow things down, but it's not looking very deep. If a bad actor shows up with a seemingly legitimate ID, they're likely getting in.
This approach offers a very basic layer of security, but it just doesn't have the smarts to catch more sophisticated threats. It might be okay for a very small business with minimal exposure, but it’s easily outmatched in today's threat-heavy environment.
As cyber threats evolved, so did firewalls. The next step up is the Stateful Inspection Firewall. Now, imagine that security guard got an upgrade. They don't just check IDs; they also remember who is already inside the building and what they’re doing. These firewalls track active connections, making sure that any data coming into your network is a direct response to a request made from within.
This added "context" is a huge leap forward. The firewall essentially knows if a data packet is part of an ongoing, legitimate conversation. It stops attackers from just blindly sending malicious data to your network, offering a much more solid defense than simple packet filtering.
The image below shows how these technologies build on one another, from basic filtering to much more advanced threat prevention.
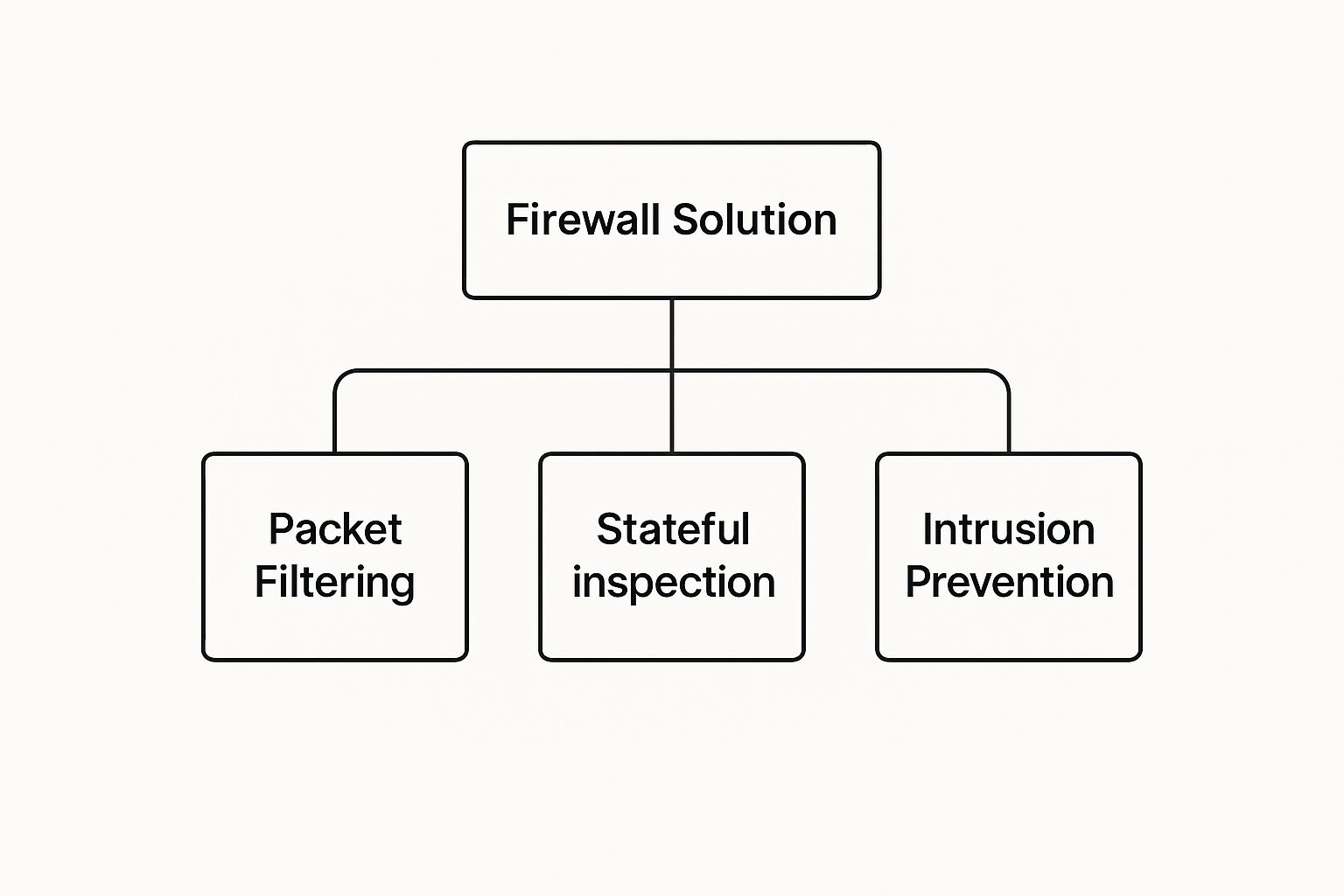
While each layer adds to the last, real security comes from weaving these capabilities together into a more powerful, cohesive system.
For most businesses today, though, even stateful inspection isn’t quite enough. That brings us to the top tier of modern protection: the Next-Generation Firewall (NGFW).
An NGFW is less like a single guard and more like a complete security detail. It still checks the IDs and remembers the conversations, but it also runs background checks, analyzes behavior, and taps into real-time threat intelligence to shut down sophisticated attacks before they can do any harm.
What sets NGFWs apart is their ability to perform deep packet inspection, meaning they can actually look inside the data. This allows them to spot malware, block access to malicious websites, and even control which specific applications are allowed to run on your network. That kind of visibility is absolutely essential for defending against the threats businesses face today.
Hardware vs. Software vs. Cloud: Where Does Your Firewall Live?
On top of deciding how your firewall inspects traffic, you also have to choose how it's deployed. There are three main models, and it's not uncommon for businesses to use a mix of them to get full coverage.
Comparing Key Firewall Types for Modern Businesses
The table below breaks down the core features, protection levels, and ideal use cases for the main categories of firewall solutions available today.
| Firewall Type | Protection Level | Key Feature | Best For |
|---|---|---|---|
| Hardware Appliance | Network Perimeter | A dedicated physical box that sits between your internal network and the internet, protecting all devices within the office. | Securing a central office location and providing a strong, first line of defence for the entire network. |
| Software Solution | Individual Device | An application installed directly onto endpoints like laptops, servers, or workstations. | Protecting remote employees' devices when they are outside the corporate network or adding an extra layer of security to critical servers. |
| Cloud-Based (FWaaS) | Distributed Networks | A service delivered from the cloud that protects all assets, regardless of location—including cloud servers, remote offices, and mobile users. | Businesses with significant cloud infrastructure, a large remote workforce, or multiple branch offices that need consistent security policies. |
Ultimately, the right deployment model comes down to your operational reality.
For a startup running entirely out of a single office, a powerful hardware firewall at the perimeter might be the perfect solution. But for a larger enterprise with employees all over the place and a heavy reliance on cloud services, a cloud-based Firewall-as-a-Service (FWaaS) makes a lot more sense. FWaaS gives you one central point of control to enforce consistent security policies for every user and every device, no matter where they are.
Choosing the right firewall is a strategic decision that shouldn’t be rushed. By understanding these fundamental differences, you can properly assess your company's unique needs and select a defense that will truly protect your most valuable assets.
How Firewalls Build Digital Trust and Business Resilience

A strong firewall does much more than just block bad traffic. It’s a cornerstone of your business's reputation. Think about it: every time we hear about another major data breach, customers and partners get a little more cautious. They aren't just looking for good products anymore; they're looking for businesses they can trust with their information.
This reality turns cybersecurity from a necessary expense into a real competitive edge. A solid firewall tells the world you’re serious about security, making you a far more attractive and reliable partner. It’s a move that’s not just about defense, but about building a brand that lasts.
From Technical Tool to a Pillar of Trust
It's easy to see a firewall as just another piece of tech, but that view misses the bigger picture. Every single attack it stops doesn't just protect your data—it protects your credibility. When customers hand over their personal information, they are placing their trust in you.
Having an advanced firewall in place is how you prove you're worthy of that trust. In the Middle East especially, this idea of "digital trust" is becoming a make-or-break asset. A recent PwC survey found that a massive 73% of organizations now view cybersecurity as a core part of building customer confidence. Your security measures, or lack thereof, directly impact your brand’s value.
A firewall is not just a defensive measure; it is a proactive statement. It tells your clients, partners, and stakeholders that their security is a top priority, fostering the long-term relationships that are vital for business success.
Investing in a proper security strategy, then, is really an investment in your brand identity. It’s what can set you apart from competitors, helping you win over and keep clients who know exactly what’s at stake online.
Ensuring Continuity in a Volatile Environment
Beyond reputation, firewalls are fundamental to business resilience. All it takes is one successful cyberattack to bring your operations to a dead stop. The fallout isn’t just about the immediate financial hit; it’s about regulatory fines, logistical nightmares, and damaged supplier relationships that can take months, or even years, to repair.
A modern firewall is designed specifically to keep your business running by neutralizing threats before they can cause that kind of damage. This protection is what lets you maintain stability in a world that’s anything but.
- Preventing Downtime: A good firewall keeps your essential systems online by blocking disruptive threats like DDoS attacks and ransomware.
- Protecting Core Assets: It acts as a guard for your most valuable data, from intellectual property and financial records to operational plans.
- Enabling Secure Growth: With a secure network, you can confidently embrace new technologies and expand your business without exposing yourself to unnecessary risk.
Ultimately, a firewall gives you the freedom to operate with confidence. It provides the stability you need to navigate digital threats and keep serving your customers without a hitch. For a deeper look into this topic, you might be interested in our guide on how to keep your business network secure and reliable. This kind of resilience is what separates the businesses that thrive from those that just get by.
Putting an Effective Firewall and Security Strategy in Place

Just having a firewall isn't enough. It's the starting line, not the finish line. To get the most out of it, you need a clear, ongoing plan. An out-of-the-box setup might catch the most obvious threats, but it often leaves behind subtle gaps—and you can bet determined attackers will find them.
A truly solid defense means treating your firewall not as a static box, but as a living part of your security that needs to adapt. This requires shifting from a "set it and forget it" attitude to one of active, hands-on management.
Start With a Thorough Risk Assessment
Before you can build a wall, you need to know what you're protecting and who you're protecting it from. That’s why a comprehensive risk assessment is the absolute first step. This isn't just a technical exercise; it's about identifying your company's crown jewels—be it customer databases, financial records, or intellectual property—and figuring out how they could be compromised.
This process forces you to answer the tough questions: Where does our most sensitive data live? Who really needs access to it? What are the most common attack methods in our industry? The answers you find will become the blueprint for your firewall's rulebook.
Get Professional Help With Configuration and Rule Management
Automated setups are tempting, but they tend to be overly generous with permissions, punching holes in your security you might not even see. Professional configuration is vital for establishing a "principle of least privilege." In simple terms, this means your firewall blocks everything by default and only allows the specific traffic your business absolutely needs to function.
But that initial setup is just day one. A firewall's rule set must be treated like a living document.
An outdated or cluttered rule set can quickly turn your firewall from an asset into a liability. Regular reviews are crucial for cleaning out old rules, tightening existing ones, and adapting to new business needs. It’s what keeps your shield strong.
Consistent audits prevent "rule bloat" and seal up security gaps that naturally appear as your business evolves. It’s no different from changing the locks when an employee leaves—you wouldn't leave an old key active, and the same logic applies to your network.
Make Your Firewall Part of a Layered Defense
A firewall is a formidable tool, but it should never be your only one. The most effective security strategies are built in layers, with different tools working in concert. When your firewall is integrated with other security solutions, you create a far more intelligent and responsive defense system.
Some of the most important integrations include:
- Intrusion Detection/Prevention Systems (IDS/IPS): Think of these as the security guards watching the traffic your firewall lets through. They spot suspicious behavior and can tell the firewall to block a threat instantly.
- Security Information and Event Management (SIEM): A SIEM system is your central security dashboard. It gathers logs from your firewall and other devices, piecing together clues to spot sophisticated, coordinated attacks.
- Endpoint Protection: Combining firewall intelligence with security on your actual computers and servers ensures that threats are contained, whether they come from an external attacker or an infected device already inside.
The growing investment in cybersecurity across the region underscores just how critical this is. The Middle East and Africa (MEA) cybersecurity market is expected to grow at 12.1% annually, with hardware like firewalls representing the biggest piece of that spending. You can learn more about the trends shaping the MEA cybersecurity market. Working with a local partner for expert IT support in Abu Dhabi can help ensure your strategy is built and managed correctly from the ground up.
Common Questions About Business Firewall Solutions
Even when you understand why firewalls are crucial, a lot of practical questions come up when you start thinking about the day-to-day reality. Getting straight answers to these is the key to feeling confident about the security choices you make for your business.
Let's dive into some of the things we hear most often.
Is the Firewall From My Internet Provider Good Enough?
This is a big one. The short answer? No, not for a business. While the basic firewall your internet service provider (ISP) gives you is better than nothing, think of it as a simple screen door. It's not built for the kind of serious protection a business needs.
Those ISP-provided firewalls just don't have the muscle for today's threats. They're missing critical features like deep packet inspection, application control, and real-time threat intelligence. A dedicated, business-grade firewall gives you the robust, fine-tuned control necessary to truly protect your sensitive data and keep your operations running smoothly.
How Often Do I Need to Update My Firewall?
Another common concern revolves around maintenance. A firewall isn't a slow cooker; you can't just set it and forget it. Its effectiveness depends entirely on keeping it current. Software and threat definitions must be updated the moment a patch is released by the vendor.
Just as importantly, the actual rules that tell the firewall what to block and what to allow need to be reviewed at least quarterly. You should also revisit them anytime you make a significant change to your network, like adding a new server or service.
A firewall is only as good as its last update and its current rulebook. Outdated rules can create security holes just as dangerous as having no firewall at all. Regular, disciplined maintenance is simply not optional.
Staying on top of this ensures your security policies are always aligned with your business and ready for the latest threats. For many companies, the easiest way to manage this is with a structured plan, like a yearly maintenance contract, which brings in experts to handle it for you.
What’s the Real Difference Between Hardware and Software Firewalls?
Finally, people often wonder whether they need a physical box or just a program. A hardware firewall is a dedicated physical appliance that sits between your internal network and the outside world, acting as a powerful gatekeeper for your entire office.
A software firewall, on the other hand, is a program installed directly onto an individual device, like a laptop or a server.
Each plays a specific and important part:
- Hardware Firewalls: Perfect for establishing a strong defensive perimeter for a central office network.
- Software Firewalls: Essential for protecting individual devices, especially for remote workers, and for adding an extra layer of security on critical internal servers.
The best strategy today is often a hybrid one. By combining a powerful hardware firewall at the office with software firewalls on all employee devices, you create a layered defense that protects your team and your data, no matter where they're working.
Ready to secure your business with a firewall solution built for today's threats? The expert team at OMX Solutions L.L.C. can design, implement, and manage the perfect security strategy for your needs. Protect your business today by visiting us at https://omxsolutions.com.
